What are Rogue Access Points and how Rogue Access Points are detected & blocked
 Rogue Access Points:
Rogue Access Points:
Sometimes, an employee, or a guest might bring along inexpensive consumer grade access points and connect them to the corporate LAN to get wireless access. This can happen if the company does not provide wireless access (or) can be done by guests with malicious intent. Of course, roghe access points might be brought in and connected even when a corporate wireless network is in place.These type of access points that do not belong to the corporate wireless network but still attached to the (wired) corporate network, are called Rogue Access Points.
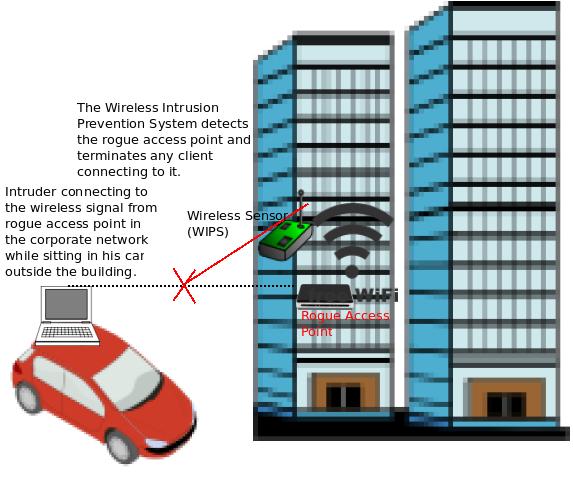
If a rogue access point is in place, there is no guarantee that it will have password protected access (or) it will use encryption to protect the wireless communications. So, some one sitting in a car in the nearby street can get these signals and can get access to the corporate network directly if there is no password protection, and using software tools like wireless sniffers, if there is password protection but no encryption. This way the intruder can get access to corporate information (or) can use obtained information to carry out some wireless attacks on the network.
How Rogue Access Points are identified by Wireless Intrusion Prevention Systems (WIPS):
Wireless Intrusion Prevention Systems identify such rogue access points by correlating all the MAC addresses (of access points) obtained from the wired network (eg. Switch CAM table) and the wireless network. If certain Access Point MAC addresses are present on both wired and wireless sides but still are not among the list of authorized access points employed by the company (if there is a corporate wireless network), then they are classified as rogue access points. Some WIPS systems can also inject certain signature packets in the wired and wireless networks and monitor which access points forward them between the two networks, to identify whether the access points are connected to the wired network.
How WIPS Systems prevent Rogue Access Points from causing any damage:
Wireless Intrusion Prevention Systems can also block such rogue access points by employing WIPS sensors to disconnect the client’s connection with the rogue access points by sending spoofed disconnection frames (De-Auth frames) continuously. When they do that, the client’s think that this AP is no longer available and hence do not connect with it, at least temporarily. Certain WIPS systems can also locate the switch port to which the rogue access point is connected, and disable the switch port using SNMP (for example), if the wired network allows for such integration. These are the commonly used methods to block the rogue access point communications but few vendors might employ some additional techniques, as well.
excITingIP.com
You can stay up to date on the various computer networking technologies by subscribing to this blog with your email address in the space mentioned as “Get Email updates when new articles are published”.