How IEEE 802.1x secures the Network edge
The Network Access to the IT network of any organization needs to be controlled right at the network edge – where the devices connect to the IP Network. In this article, let us look at an introduction to IEEE 802.1x protocol, the elements of 802.1x, advantages of 802.1x, role of 802.1x in the authentication of the network connectivity requests and why network switches needs to support this open standard protocol.
What is IEEE 802.1x and why is it required?
Well, consider this – an organization has a huge computer network spanning multiple geographies. There may be hundreds of computer users connecting to this network by running a cable between the Ethernet Network Switches and the Ethernet Port of the Desktop/ Laptop. If this network has an open access to everyone, then the guests or contractors coming to the conference room for example, can simply plug in their laptops to the empty RJ-45 ports available there and start accessing the network resources! Now let us bring the wireless networks in to the picture – people need not even enter the premises of the organization to access the organization’s wi-fi network! Obviously, one does not want this to happen – So, it becomes important for organizations to control which endpoints (PC’s etc) want to access which network resources (Internet, Servers etc). IEEE 802.1x helps networks do exactly that – Authentication of the users connecting to the network and setting basic network policies (access control).
In short, IEEE 802.1x is an open standard (vendor neutral) protocol which provides the structure of the type of messages that can be exchanged by the users (PC’s Laptops etc) wanting to connect to the network through Network Switches & Access Points prior to their authentication/ authorization with the Radius Servers/ AD so that only the genuine users attached to the organization can be allowed to connect to and access the network resources.
Advantages of IEEE 802.1x Protocol:
- IEEE 802.1x is an open standard protocol and hence is vendor neutral – This attribute is highly desirable for big multi-vendor network deployments.
- IEEE 802.1x supports multiple authentication methods like User name/passwords, token cards, OTP – One Time Passwords, Public Key Infrastructure Certificates, Certificates from external CA’s etc. It also allows room for addition of newer authentication methods in the future.
- Both Wired and Wireless network connections can be authenticated using this standard.
- Multiple types of endpoints can be authenticated using IEEE 802.1x – For example, PC’s, Laptop’s, PDA’s, IP Phones, Network Surveillance Cameras etc.
- It allows for encryption of the messages being transmitted between the endpoints and the network switches/ access points so that it becomes difficult for intruders to get authentication credentials by sniffing in to the network.The encryption keys can be changed dynamically in some 802.1x methodologies.
- IEEE 802.1x is useful for companies that have network points in public places (reception, cafe, conference rooms) and very useful in case of wireless networks & public hot-spots.
- It allows for having separate VLAN’s for guests, for example, and as soon as they connect to the network they could be given limited access to network resources with policies applied to them like Internet Access only etc.
- The authentication and network access management is centralized and hence the IT personnel sitting at the HO can manage multi-site networks.
Elements of an 802.1x Network:
There are three main elements of an IEEE 802.1x process,
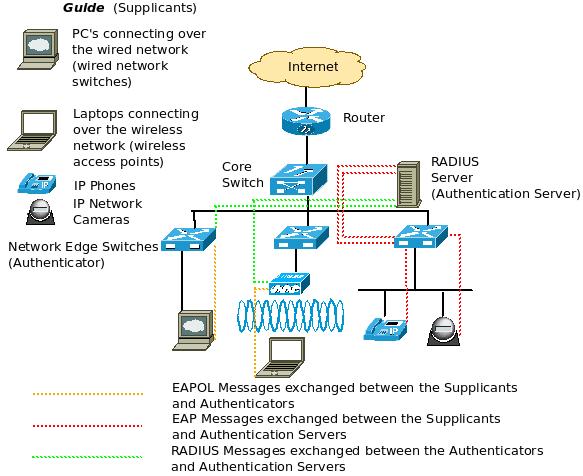
1. Supplicant – PC, Laptop, PDA, IP Phone, IP Network Camera and any other device wanting to connect to the network is referred to a Supplicant.
2. Authenticator – The Network Switches/ Wireless Access Points providing the first level connection to the supplicants is termed as an Authenticator.
3. Authentication Server – Any server/ device that can hold the authentication credentials for all the users (supplicants) and verify them against the provided information by end points during the authentication process is termed as an Authentication Server (RADIUS server, AD etc).
Main Protocols / Authentication Process in IEEE 802.1x
There are many protocols supported by the 802.1x standard and the main one among them all is EAP – Extensible Authentication Protocol. In fact, EAP is only a standard to exchange the authentication messages between the various elements in an 802.1x authentication process. If this protocol is supported by Supplicants, Authenticator and Authentication Server, then it becomes easy for requesting and challenging the authentication credentials and in many cases only the EAP messages are allowed to traverse the network from new supplicants (end points) wanting to connect to the network, and not yet authenticated.
Initially, the messages between a supplicant and a authenticator is passed in the form of EAPOL (Extensible Authentication Protocol Over LAN) and the Authenticator converts them in to RADIUS messages and sends it to a RADIUS server (Authentication Server). The Authentication Server then negotiates the type of EAP authentication that is acceptable to both the supplicant and itself and starts communicating with the supplicant via EAP messages to carry out the authentication process. Some authenticators may not support all types of EAP and hence would act as an EAP pass through where the supplicants directly communicate with the Authentication Servers to complete the authentication process.
Before the authentication happens, the authenticator sets the network port to the Uncontrolled State where in only the EAP / EAPOL messages are allowed to pass through between the supplicants and the authentication server. All other traffic remains blocked from that network port. But after the authentication, the network port is set to Controlled/ Authorized State to grant network access according to the NAC policies.
Types of EAP Protocols:
EAP – Extensible Authentication Protocol is very flexible in which there are multiple types of authentication mechanisms supported and the administrator can choose between them (Or even a combination) for authenticating the users wanting to connect to the network. For example, User name/ Passwords and MAC address based authentication can be combined using EAP and a device can be allowed to access the network devices only if both user-name password and MAC address from which they are connecting to, matches the previously stored values in the authentication server. This makes the process more secure, and the methods can be changed as per the user/ device or other parameters.
The following are the main types of the EAP protocol:
EAP-MD5 (EAP – Message Digest 5) : This is one of the basic methods used for authentication and EAP-MD5 uses user name/ password combination for verifying the authentication credentials. EAP-MD5 offers basic protection for the messages exchanged by creating a digital fingerprint to digitally sign all the packets but no strong authentication methods are used. Hence is it less secure and can be used in wired networks needing basic security and ease of configuration and implementation.
EAP-TLS (EAP – Transport Level Security) : In this method, both the client and authentication server needs to have pre-installed PKI certificates (Digital Certificates) in order for them to be mutually authenticated. Since pre-installed certificates are required and a TLS Tunnel is created between the authentication server and client, this method is more secure and used for wireless networks and wired networks in an environment where majority of the stations come with pre-installed certificates. Otherwise, loading the certificates in all the clients could become a cumbersome activity. For certain special devices like IP Phones, Network Surveillance Cameras etc, EAP-TLS comes in very handy as these devices cannot use user-name password credentials but can use pre-installed certificates to authenticate themselves with the authentication servers. Many vendors support EAP-TLS / 802.1x on such devices and it is recommended to authenticate them by this method instead of allowing open access.
EAP-TTLS (EAP – Tunneled TLS): In this method, the clients authenticate to the authentication servers using user-name/passwords but the mutual authentication by PKI certificates is not required for the clients – It is sufficient if the authentication servers authenticate to the clients using their certificates. TLS Tunnels are created to protect the authentication messages and this method is secure and easy to roll out. In fact, it also supports existing user credential services such as Active Directory, LDAP, RADIUS server etc to be re-used for 802.1x authentication and is also backward compatible with PAP, CHAP, MS-CHAP and other authentication protocols.
excITingIP.com
In case you want to add some points to this topic, or have any questions, please feel free to interact with us using the comment box below or by using the Contact-Form. You could also stay up to date on the various important topics in the computer networking industry by subscribing with your email address – The Email Subscription box can be found in the right hand side of this website (For IE users it may be below).
very useful information, as i always wondered what this network protocol was for. look forward to receiving updates through email. thank you